Cado Security is the provider of the first cloud forensics and incident response platform. By leveraging the scale and speed of the cloud, the Cado platform automates forensic-level data capture and processing across cloud, container, and serverless environments. Only Cado empowers security teams to respond at cloud speed. Backed by Eurazeo, Blossom Capital, and Ten Eleven Ventures, Cado Security has offices in the United States and the United Kingdom.
Captured by Cado
Investigating Serverless and Container Attacks with Cado Community Edition
Captured by Cado is a Capture the Flag (CTF) challenge series designed to educate incident responders on how to investigate attacks on cloud-based systems. This challenge is specifically focused on investigating three attack scenarios in Lambda serverless functions and ECS container systems.
In this webinar,
you’ll learn:
- How to leverage key features in the Cado Community Edition to speed up investigation and response
- How bad actors are compromising serverless and container environments
- How to analyze various evidence captured from Lambda functions and its associated logs and ECS container instances
View On Demand
Want to flex your skills?
See if you can solve the CTF challenge using the Cado Community Edition before the webinar.
Step 1
Install the Cado Community Edition
Step 3
Upload the files to the S3 bucket for your deployment (you can find the identifier in the AWS Console under CloudFormation – Stacks – <stack name> – Outputs – S3Bucket)
Step 5
In each project, click Import – Artifacts from S3, and import the following files into their respective projects
Step 2
Download the files in the GitHub repository
Step 4
Create two projects – named Lambda CTF and ECS CTF
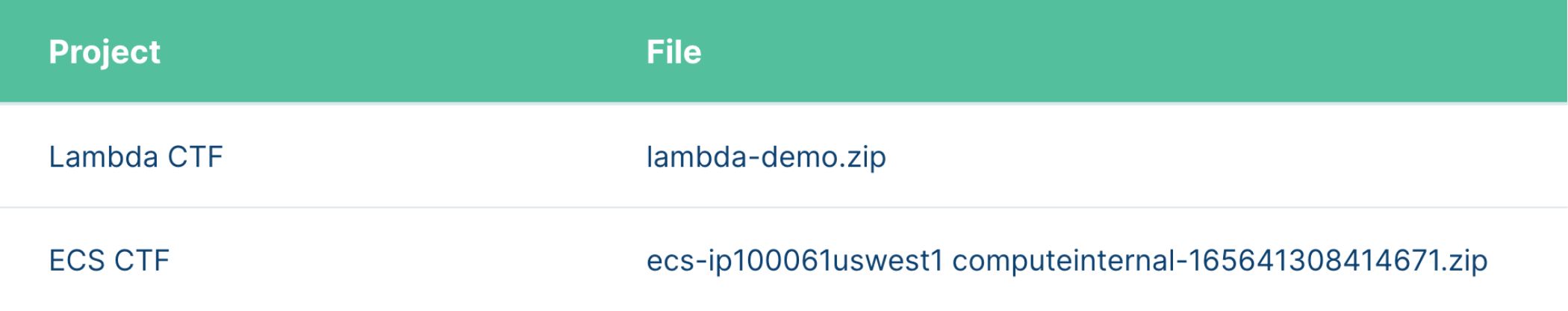
Lambda CTF
Looking in the AWS Console, you discover a Lambda function that nobody knows anything about.
You use the Cado platform to acquire the Lambda function and its associated logs and immediately find that it’s a cryptominer running in Lambda.
Questions to answer
- What are the three URLs embedded in the script?
- When was the first time this function was run?
ECS CTF
The AWS Console also shows some containers that request way more vCPU resources than your standard containers do.
You use the Cado platform to acquire the container, and again, you find that someone installed a cryptominer.
Questions to answer
- What users did the attacker create?
- What command did the attacker run from Pastebin.com?
- How did the attacker find out what the external IP address of the system was?
- BONUS: What might be some additional data you want to collect to understand more?